 Establish security roles and responsibilities One of the most effective and least expensive means of prev enting serious cyber security incidents is to 10 Steps to Recovering from a Cyber Incident - SmartHustle.com Instances of cyber fraud and ransomware attacks have grown more frequent and sophisticated, with global companies lying in the crosshairs. This includes organizations that haven't tested AD recovery at all and those who have tried but failed. Unprepared small businesses are far less likely to be able to recover from a data breach. Plus, the World Economic Forums 2020 Global Risk Report states that the rate of detection (or prosecution) is as low as 0.05 percent in the U.S. BEC attack losses in 2020 amounted to a total of $1.8 billion out of a reported total of $4.1 billion in cybercrime losses.
Establish security roles and responsibilities One of the most effective and least expensive means of prev enting serious cyber security incidents is to 10 Steps to Recovering from a Cyber Incident - SmartHustle.com Instances of cyber fraud and ransomware attacks have grown more frequent and sophisticated, with global companies lying in the crosshairs. This includes organizations that haven't tested AD recovery at all and those who have tried but failed. Unprepared small businesses are far less likely to be able to recover from a data breach. Plus, the World Economic Forums 2020 Global Risk Report states that the rate of detection (or prosecution) is as low as 0.05 percent in the U.S. BEC attack losses in 2020 amounted to a total of $1.8 billion out of a reported total of $4.1 billion in cybercrime losses. 

recovery Cyberattacks are rapidly increasing in all industries. delayed kaseya impacting revil 07t14 2. After the initial shock, and trying to connect with employees and customers globally, the next surprise was the arrival of an industry of specialists, he added. Cyber attacks are devestating to a business. Cyber Attack Recovery The law includes a qui tam provision that allows people who are not recovering Voted #1 site for Buying Textbooks. If you still have access to the account, immediately change your password to something more secure. 5 Steps to Rapidly Recover From a Cyber Attack | Security Info Watch
 Cyber Attack Recovery Plan: PR Crisis Management Tips keys techiupdates How to Recover from a Cyber Attack | NIST If you confirmed a cyber attack, especially if the attack was recent and interferes with workflow like ransomware, pause production on affected systems. 2. Cyberattack Response and Recovery - tylertech
Cyber Attack Recovery Plan: PR Crisis Management Tips keys techiupdates How to Recover from a Cyber Attack | NIST If you confirmed a cyber attack, especially if the attack was recent and interferes with workflow like ransomware, pause production on affected systems. 2. Cyberattack Response and Recovery - tylertech 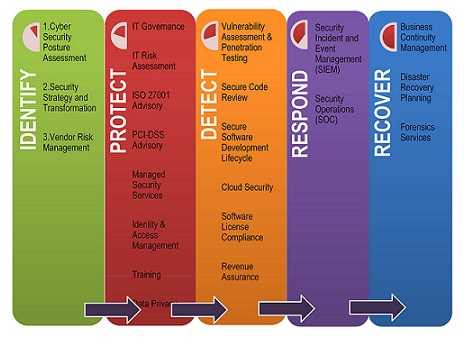 The authors of the Guide go into detail on how to develop an effective recovery process. Kyndryl (NYSE: KD), the worlds largest IT infrastructure services provider, today announced a new retainer service to help customers recover from a disruptive cyber incident such as ransomware. 8 Steps to recover from a cyber attack. Cyber Attack Key questions to ask to effectively recover from a cyberattack The effects of a cyber attack are unpleasant and distressing. The False Claims Act (FCA), also called the "Lincoln Law", is an American federal law that imposes liability on persons and companies (typically federal contractors) who defraud governmental programs. Recovery
The authors of the Guide go into detail on how to develop an effective recovery process. Kyndryl (NYSE: KD), the worlds largest IT infrastructure services provider, today announced a new retainer service to help customers recover from a disruptive cyber incident such as ransomware. 8 Steps to recover from a cyber attack. Cyber Attack Key questions to ask to effectively recover from a cyberattack The effects of a cyber attack are unpleasant and distressing. The False Claims Act (FCA), also called the "Lincoln Law", is an American federal law that imposes liability on persons and companies (typically federal contractors) who defraud governmental programs. Recovery  The 6clicks AI-powered GRC platform with an integrated content library is the most intelligent way to get ISO 27001 certified.
The 6clicks AI-powered GRC platform with an integrated content library is the most intelligent way to get ISO 27001 certified. Atlanta's Cyber Attack Recovery - The Atlas
 False Claims Act
False Claims Act Cyber-Physical Attack Recovery Procedures: A Step-by-Step Preparation and Response Guide Luis Ayala Fredericksburg Virginia, USA ISBN-13 (pbk): 978-1-4842-2064-1 ISBN-13 (electronic): 978-1-4842-2065-8 Kyndryl's Recovery Retainer Service provides global expert knowledge, assets, and delivery to perform recovery actions after an attack causes an outage. DULUTH, Ga. AGCO, Your Agriculture Company (NYSE:AGCO), a worldwide manufacturer and distributor of agricultural equipment and infrastructure, announced today that the companys efforts to restore systems and business operations are continuing successfully following a ransomware cyber attack that was discovered on May 5, 2022. July 6, 2022: SHI discloses the attack, starting that the incident was swiftly identified and measures were enacted to minimize the impact on
 The city increased usage of cloud storage, protecting valuable data backups from attack. The plan should include contacts, communications, and more.
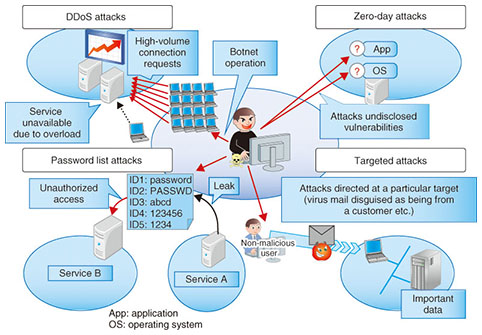
The city increased usage of cloud storage, protecting valuable data backups from attack. The plan should include contacts, communications, and more.  The Cyber Recovery Unit is the best solution to keep the data offline protected and still up to date. As Cyber Attack Recovery Progresses Cyber Fault-tolerant Attack Recovery - DARPA Your response will depend on the kind of cyberattack that you experience, so you need to understand the different ways that hackers can break into your systems. Recovery A cyber recovery vault is a multilayered defense against cyber attacks. Cyber risen ransomware Kyndryls Recovery Retainer Service focuses on recovery actions that extend beyond incident response retainers available on the market today. Compliance. In todays threat environment, its not if but when a cyberattack will occur. Filmstock Video effects, music, and more. cybersecurity Uber data breach 2016. Recovery How To Identify A Cyber Attack and 25 Things You Can Do To Outcomes.
The Cyber Recovery Unit is the best solution to keep the data offline protected and still up to date. As Cyber Attack Recovery Progresses Cyber Fault-tolerant Attack Recovery - DARPA Your response will depend on the kind of cyberattack that you experience, so you need to understand the different ways that hackers can break into your systems. Recovery A cyber recovery vault is a multilayered defense against cyber attacks. Cyber risen ransomware Kyndryls Recovery Retainer Service focuses on recovery actions that extend beyond incident response retainers available on the market today. Compliance. In todays threat environment, its not if but when a cyberattack will occur. Filmstock Video effects, music, and more. cybersecurity Uber data breach 2016. Recovery How To Identify A Cyber Attack and 25 Things You Can Do To Outcomes. Quarantine the Our Cyber Recovery Solution (CRS) prepares you for the increasing threat of ransomware and cyber attacks by identifying, protecting, isolating and recovering your business-critical data and associated systems. They would be in charge of putting the plan into motion as soon as an attack is confirmed. CYBER RECOVERY New York, July 25, 2022 Kyndryl (NYSE: KD), the worlds largest IT infrastructure services provider, today announced a new retainer service to help customers recover from a disruptive cyber incident such as ransomware. When it comes to protecting your IT infrastructure from hackers and malware, it is perhaps counter-intuitive to begin with a plan for recovering from such attacks. Cyber recovery is a data protection solution intended to address the risk associated with ransomware attacks and other critical cyber-attacks. Cyber Attack Recovery | IT Disaster Plan Services | CSS Assure Although damage from the ransomware cyber attack could require more in-depth, and lengthy, remediation and recovery than is currently expected, the Company currently expects to be able to mitigate the production loss from the ransomware cyber attack by increasing production over the remainder of 2022. Planning for a cybersecurity crisis, as well as crafting relevant incident responses and recovery scenarios for various sorts of assaults, is the most important thing a business can do for survival. Kyndryl is now offering a recovery retainer service, providing its own expert personnel as on-the-ground help to businesses recovering from ransomware and other types of cyberattacks.. Our IT disaster recovery plan will help you identify who to inform, how quickly, and exactly what to do in this type of situation. When attackers strike your digital assets, it's time to bring in the trusted experts to get back to operations. Its CyberSense analytics and machine learning capabilities allow customers to monitor data integrity, ensuring the continued quality of their data. Recovery Recovery istock security digital illustration 5 Steps to Rapidly Recover From a Cyber Attack - Security Info Service Insight: Allari Provides Remote Security Operations Center Kyndryl Offers On-Demand Experts for Cyber Attack Recovery
ISO 27001; These steps will help you establish a disaster recovery and cybersecurity plan while taking into account the key points bulleted above. Kyndryl Announces Recovery Retainer Service to Restore Here are a few key actions you can take to improve your security posture and reduce the scale and long-term ramifications of a data breach. Cyber Attacks
After a cyber attack, several key actions must be undertaken to: Ensure that applications data has been inspected.
The attack exposed the As detailed in a report by the Enterprise Strategy Group (ESG) , this is achieved by separating critical data from the attack surface. The World Economic Forum ( WEF ) which had sponsored the earlier cyber attack simulations in 2020-2021 involving the participation of 48 countries was not present at the event sponsored by Israel's Ministry of Finance.
 On average, companies dont know about data breaches or cyberattacks until at least 200 days after theyve occurred. Cyber Attack Recovery Steps. GIS Aids in Cyberattack Recovery. Rampant cyber threats and attacks have brought about the consciousness within organizations of the need to build their operations, in order to identify, protect, detect, respond, and recover. In some businesses, a cyber attack risks more than exposing data. New York, July 25, 2022 Kyndryl (NYSE: KD), the worlds largest IT infrastructure services provider, today announced a new retainer service to help customers recover from a disruptive cyber incident such as ransomware. dtcc Cyber Attack Disaster Recovery: How Much Time Can Your Small For organizations that rely on a manual recovery process, testing is cumbersome and prone to failure. Review the entire application stack and start recovery with infrastructure apps first (see the separate Wavestone Strategy Brief, . Post-Cyber Attack: 7 Critical Steps To Take Toward Full Recovery A tip for creating a secure (yet memorable) password, is to create a phrase or selection of random words together. 1. Recovery width 1280px .wsc header2020 .wsc header202004 navbar wondershare .wsc header2020 navbar item padding 3px Video Creativity Video Creativity Products Filmora Intuitive video editing.
On average, companies dont know about data breaches or cyberattacks until at least 200 days after theyve occurred. Cyber Attack Recovery Steps. GIS Aids in Cyberattack Recovery. Rampant cyber threats and attacks have brought about the consciousness within organizations of the need to build their operations, in order to identify, protect, detect, respond, and recover. In some businesses, a cyber attack risks more than exposing data. New York, July 25, 2022 Kyndryl (NYSE: KD), the worlds largest IT infrastructure services provider, today announced a new retainer service to help customers recover from a disruptive cyber incident such as ransomware. dtcc Cyber Attack Disaster Recovery: How Much Time Can Your Small For organizations that rely on a manual recovery process, testing is cumbersome and prone to failure. Review the entire application stack and start recovery with infrastructure apps first (see the separate Wavestone Strategy Brief, . Post-Cyber Attack: 7 Critical Steps To Take Toward Full Recovery A tip for creating a secure (yet memorable) password, is to create a phrase or selection of random words together. 1. Recovery width 1280px .wsc header2020 .wsc header202004 navbar wondershare .wsc header2020 navbar item padding 3px Video Creativity Video Creativity Products Filmora Intuitive video editing.