Active Directory You want to use AGDLP to give Read/Write Permissions to a folder on a network share. DHCP Best Practices: The Ultimate Guide IAM also lets you create custom IAM roles.Custom roles help you enforce the principle of least privilege, because they help to ensure that the principals in your organization have only DSRM allows an administrator to repair or recover to repair or restore an Active Directory database. It works fine in a local directory but when I run the same code on a server directory it fails after about printing 86 folder names. What is the best practices regarding this, applying AGDLP? Open the System32 directory in the Windows folder on your machine. folder directory active infrastructure user users computer
Moved the computer I want the screen saver applied to from Computers to the newly created OU Start ADTD (its called Microsoft Active Directory Topology Diagrammer on the Start Menu) 3. folder Home folder: Home folders are similar to profiles as the data in it can be accessed from anywhere. Here are the common LDAP attributes which correspond to Active Directory properties. DHCP Best Practices: The Ultimate Guide 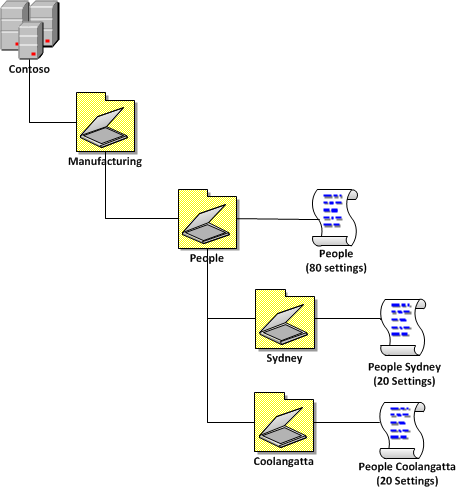 Active Directory Forest (AD Forest Each forest shares a single database , a single global address list and a security boundary. System administrators must familiarize themselves with SAM and how it works to understand, how Windows processes and stores credentials. An outage in Active Directory can stall the entire IT operations of an organization. This Active Directory group management best practices guide explains how to properly manage Active Directory distribution groups and security groups. ADAudit Plus Release Notes The best practice is to use a three-part strategy. They are useful for VBScripts which rely on these LDAP attributes to create or modify objects in Active Directory. Microsofts best practice analyzer is a tool that checks the DHCP configuration against Microsoft guidelines. System administrators must familiarize themselves with SAM and how it works to understand, how Windows processes and stores credentials.
Active Directory Forest (AD Forest Each forest shares a single database , a single global address list and a security boundary. System administrators must familiarize themselves with SAM and how it works to understand, how Windows processes and stores credentials. An outage in Active Directory can stall the entire IT operations of an organization. This Active Directory group management best practices guide explains how to properly manage Active Directory distribution groups and security groups. ADAudit Plus Release Notes The best practice is to use a three-part strategy. They are useful for VBScripts which rely on these LDAP attributes to create or modify objects in Active Directory. Microsofts best practice analyzer is a tool that checks the DHCP configuration against Microsoft guidelines. System administrators must familiarize themselves with SAM and how it works to understand, how Windows processes and stores credentials. 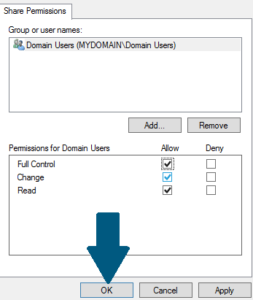 Active Directory
Active Directory
Define your inbox with color categories. 23. But, the template provides us with many different components and installed libraries, which help us achieve our goal Azure Active Directory B2C Authentication. We have already explained all of these additional components/libraries in our previous article where we talked about the Azure AD security with the Blazor WebAssembly Hosted app.
Active Directory Properties  New Feature.
New Feature.
As the table above illustrates, a group can be a member of another group; this process is called nesting. Best Practices for Outlook to Boost Your Workflow I have the following snippet of code to run through the folder and get the folder names with path. aad practice What is the best practices regarding this, applying AGDLP? Best Practices Align Google Cloud and Active Directory resource structures When you deploy a new Active Directory domain or forest on Google Cloud, you have to define an organizational unit (OU) structure to organize your resources with your Active Directory domain.
Dragged the GPO onto the newly created OU 3. Identity and Access Management (IAM) provides predefined roles that give fine-grained access to specific Google Cloud resources and help prevent unwanted access to other resources.  Microsofts best practice analyzer is a tool that checks the DHCP configuration against Microsoft guidelines. Clear selected AbhishekSharan AbrarMuhib Active Directory AdamStasiniewicz AdrianCorona AKS alanlapietra AlexRadutskiy AllenSudbring AmerKamal AndrewCoughlin AnilAbraham AnooshSaboori AnthonyMarsiglia AnthonyWatherston ArnabMitra AshleyMcGlone Azure Home; Core dashboard
Microsofts best practice analyzer is a tool that checks the DHCP configuration against Microsoft guidelines. Clear selected AbhishekSharan AbrarMuhib Active Directory AdamStasiniewicz AdrianCorona AKS alanlapietra AlexRadutskiy AllenSudbring AmerKamal AndrewCoughlin AnilAbraham AnooshSaboori AnthonyMarsiglia AnthonyWatherston ArnabMitra AshleyMcGlone Azure Home; Core dashboard
permissions ntfs As part of our continuing mission to reduce cybersecurity risk across U.S. critical infrastructure partners and state, local, tribal, and territorial governments, CISA has compiled a list of free cybersecurity tools and services to help organizations further advance their security capabilities.
Features
2. Active Directory B2C with Blazor WebAssembly Hosted Apps 2) Publish shared folders in Active Directory so that users can search for them in the directory and access them instead of having to browse the network to find them. Active Directory Properties Your Link  Way Im setup (small home network): 1. We have already explained all of these additional components/libraries in our previous article where we talked about the Azure AD security with the Blazor WebAssembly Hosted app.
Way Im setup (small home network): 1. We have already explained all of these additional components/libraries in our previous article where we talked about the Azure AD security with the Blazor WebAssembly Hosted app.  Organize your inbox with action folders. practices virtualizing
Organize your inbox with action folders. practices virtualizing
By default, a user or administrator in one forest cannot access another forest. But, the template provides us with many different components and installed libraries, which help us achieve our goal Azure Active Directory B2C Authentication. Active Directory Certificate Services (AD Active Directory shared folders and users permissions Active Directory Forest (AD Forest Core Infrastructure and Security Blog - Microsoft Tech Community For instance if you bulk import users into Active Directory you need to include the LDAP attributes: dn and sAMAccountName. VBA - Get Folder structure directory active guidelines grouppolicy biz references Here are the common LDAP attributes which correspond to Active Directory properties. Active Directory User Objects Best Practices. share a windows folder using PowerShell directory active structure example bad guidelines grouppolicy biz
 Open the System32 directory in the Windows folder on your machine. Real time auditing for Active Directory. What is the best practices regarding this, applying AGDLP?
Open the System32 directory in the Windows folder on your machine. Real time auditing for Active Directory. What is the best practices regarding this, applying AGDLP?
 Step 1: Open Server Manager. Core Infrastructure and Security Blog - Microsoft Tech Community They are useful for VBScripts which rely on these LDAP attributes to create or modify objects in Active Directory. To share a windows folder using PowerShell, we can use the New-SmbShare command. Active Directory Groups This might save time in the moment, but ends up 2) Publish shared folders in Active Directory so that users can search for them in the directory and access them instead of having to browse the network to find them. I have the following snippet of code to run through the folder and get the folder names with path.
Step 1: Open Server Manager. Core Infrastructure and Security Blog - Microsoft Tech Community They are useful for VBScripts which rely on these LDAP attributes to create or modify objects in Active Directory. To share a windows folder using PowerShell, we can use the New-SmbShare command. Active Directory Groups This might save time in the moment, but ends up 2) Publish shared folders in Active Directory so that users can search for them in the directory and access them instead of having to browse the network to find them. I have the following snippet of code to run through the folder and get the folder names with path.
Understanding IAM custom roles - Google Cloud By default, a user or administrator in one forest cannot access another forest. To finish the database installation, restart your computer. New Feature. Right click somewhere on the right > New > Shared Folder.
Steps to run the tool. Copy and paste this code into your website. 
Credential theft attacks, malware attacks, ransomware and security breaches are a few methods that help attackers gain access to privileged accounts to a computer on a network. Do not create any additional directories in the root directory, unless you really need to. directory securing gpo 4sysops Best Practices dnsstuff 
The difference is that they dont carry the working environment or customizations. The best way to control access to Active Directory and related resources is to use Security Groups. We have already explained all of these additional components/libraries in our previous article where we talked about the Azure AD security with the Blazor WebAssembly Hosted app.
Direct User Access. Create Action Folders. permissions Dragged the GPO onto the newly created OU 3. Deploying an audit policy to specific users or assets will be challenging if you do not understand your environment or have a poor logical grouping of your resources. Active Directory User Object Organize your inbox with action folders.  Announcing real-time change auditing for Windows Active Directory, the new feature provides administrators with real-time email alerts and a live feed of alerts in the ADAudit Plus console, when critical and unauthorized changes are made to AD. Now well walk through the settings tabs to configure our data collection: Enter in a local (to you) Global Catalog Domain Controller that you can interrogate with the tool.
Announcing real-time change auditing for Windows Active Directory, the new feature provides administrators with real-time email alerts and a live feed of alerts in the ADAudit Plus console, when critical and unauthorized changes are made to AD. Now well walk through the settings tabs to configure our data collection: Enter in a local (to you) Global Catalog Domain Controller that you can interrogate with the tool.